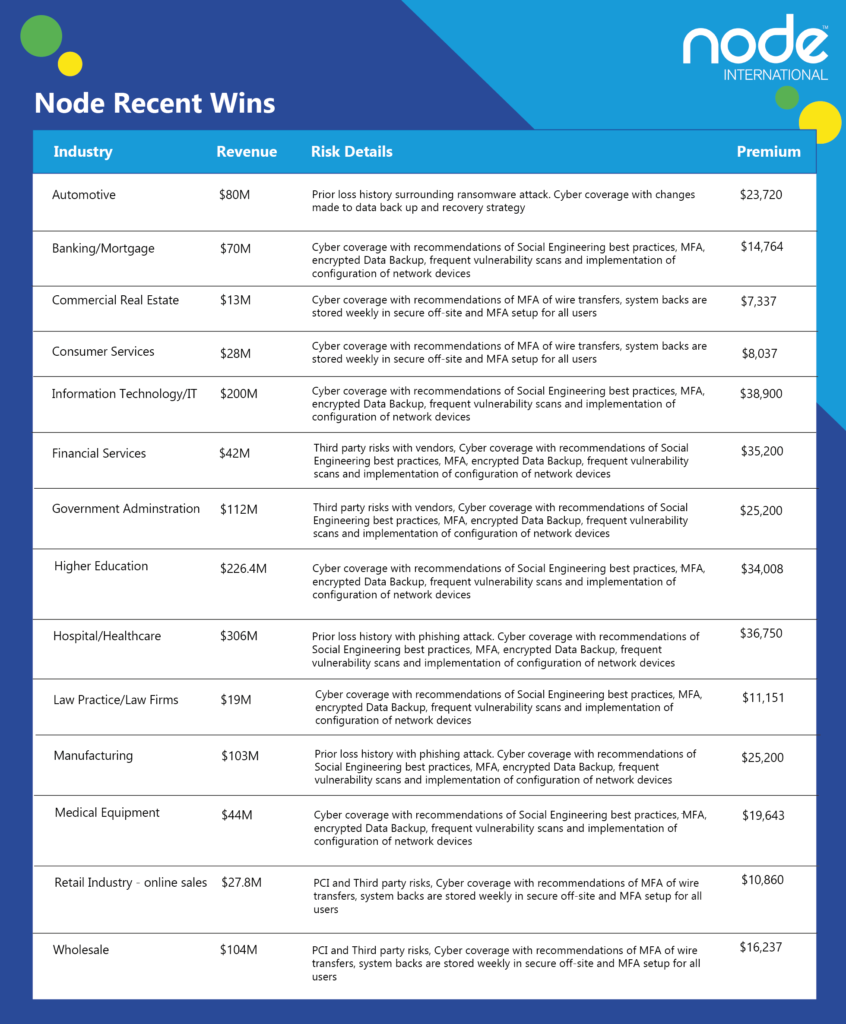
Node International would like to thank you all for your cyber submissions this quarter, here are some of our top wins we’d like to celebrate with you.
We love working with our brokers. Don’t forget to send us your cyber risks to inbox@nodeinternational and we’ll do our best to find a perfect solution.
First time working with us? Send [email protected] an email to find out more.
Does your organisation run a Microsoft Exchange Server? If so read on!
What Happened?
Microsoft has detected multiple zero day exploits attacking on-premises versions of Microsoft Exchange Server. In these attacks, the threat actor accesses on-premises Exchange servers (and the associated email accounts) and installs additional malware to retain unauthorized access to the environment.
What is Affected?
The vulnerabilities affect Microsoft Exchange Server. Exchange Online is NOT affected.
The versions affected are:
What to Do
If you run any of the affected versions, IMMEDIATELY apply these updates to affected systems to protect against these exploits. Externally facing Exchange servers should be updated first and then update all affected Exchange Servers.
Node Prevent
When you purchase one of our cyber insurance policies you’ll receive vital cybersecurity updates such as this and online training courses to keep your employees up-to-date with the current cyber threats.
According to a Pew Research Center study, 79% of U.S. adults report being concerned about the way their data is being used by companies.
By respecting your consumers’ privacy you’ll increase trust and enhance reputation and growth in your business.
How can you protect customer data:
Find out more here.
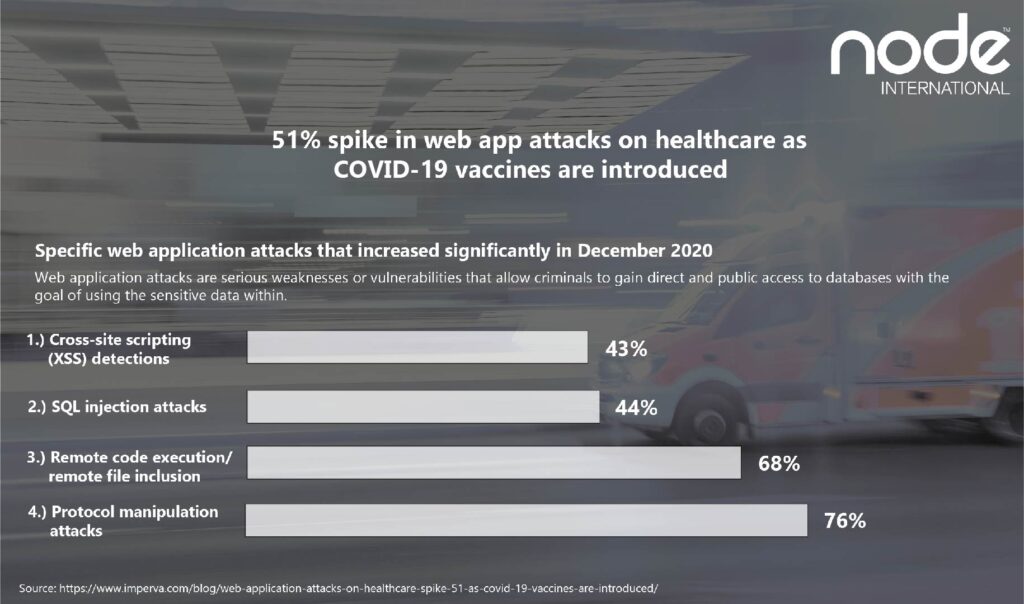
The healthcare sector experienced a surge in web application attacks in December when the distribution of the first COVID-19 vaccines began, according to new data from Imperva.
Attacks increased 51% last month from November, an industry increasingly targeted by cyber-criminals over the past year due to the global pandemic.
Web application attacks are serious weaknesses or vulnerabilities that allow criminals to gain direct and public access to databases with the goal of using the sensitive data within. Many of these databases contain valuable information such as personal data and financial details, meaning they are frequently targeted.
Four specific web application attacks saw the largest increases in December:
1.) Cross-site scripting (XSS) detections
2.) SQL injection attacks
3.) Remote code execution/remote file inclusion
4.) Protocol manipulation attack
How can healthcare organisations reduce web application attacks?
1.) Web Application Firewalls (WAFs): A vital defence for critical applications and data. WAF controls access to web applications using rules designed to recognise and restrict suspicious activity, such as SQLi, XSS and exploitation of vulnerabilities. By continuously updating the rules they are prepared to catch the latest attack and exploitation techniques before they can harm important resources.
2. Vulnerability Scanning and Security Testing: The fact web applications connect external users to data and services easily makes them big targets for attackers. Scanning and testing databases, networks and applications can help find where the vulnerabilities are and how to mitigate them.
3. Secure Development Training: Provide your developers, testers, project managers and architects with the latest information regarding secure software development. Ensure there is a baseline of security awareness so staff can confidently design, build and deploy secure software and applications.
Terry Ray, Imperva, said that 2020 has been an “unprecedented year” of cyber activity, with global healthcare organizations (HCOs) experiencing 187 million attacks per month on average. That’s almost 500 attacks per HCO each month, a 10% increase year-on-year.
The US, Brazil, UK and Canada were the top countries targeted last year.
Ray believes that Healthcare’s reliance on third-party applications to save time and money may have exposed them.
“While there are sometimes business advantages to third-party applications, the risks include: patching only on the vendor’s timeline, known exploits that are widely publicized and constant zero-day research on widely used third-party tools and APIs.”
Ray also highlighted how exploiting web application vulnerabilities is the most common cyber attacks directed at healthcare organisations.
“Reliance on JavaScript APIs and third-party applications creates a threat landscape of more complex, automated, and opportunistic cybersecurity risks that are increasingly challenging for all organizations to detect and stop. And while ransomware attacks commonly land healthcare organizations in the news, it’s only the vulnerable application front-end to all healthcare data that experiences the variety and volume of daily attacks noted above.”
In just the first three days of 2021, Imperva saw a 43% increase in data leakage.

SolarWinds, a popular IT security vendor with 300,000 global customers (including many small to medium size businesses and their Managed Service Providers), has suffered a major compromise.
If your organization uses the SolarWinds Orion Platform, READ ON. If you’re not sure, ask someone in your organization that does.
Even if you don’t use the SolarWinds Orion Platform, one of your business partners may be among the 18,000 organizations potentially affected by this breach.
SolarWinds, a popular IT security vendor with 300,000 global customers (including many small to medium size businesses and their Managed Service Providers), has suffered a major compromise.
If your organization uses the SolarWinds Orion Platform, READ ON. If you’re not sure, ask someone in your organization that does.
Even if you don’t use the SolarWinds Orion Platform, one of your business partners may be among the 18,000 organizations potentially affected by this breach.
We strongly recommend you contact all business partners with whom you share sensitive business information or allow access into your IT environment to ensure that, if they use the affected platforms, they are taking the recommended actions below.
If you are allowing an affected partner access into your IT environment, we recommend disabling that access until the issue has been remediated.
Indeed, the Cybersecurity and Infrastructure Security Agency (CISA) has advised everyone that uses the SolarWinds Orion monitoring software to assume they’ve been “compromised by threat actors and assume that further persistence mechanisms have been deployed.”
What Happened?
The compromise allowed hackers to inject malicious code into legitimate software released by SolarWinds for its Orion platform, a suite of network management tools.
This malicious code is a backdoor that communicates with command-and-control servers operated by a malicious third party.
This supply chain attack has been connected with the recent FireEye and U.S. Department of Homeland Security (DHS) hacks.
Affected organizations may have been compromised by malicious hackers as early as May 2020.
What/Who is Affected?
The compromised platforms are SolarWinds® Orion® Platform software builds for versions 2019.4 HF 5, 2020.2 with no hotfix installed, and 2020.2 HF 1.
The known affected products for these Orion Platforms are:
SolarWinds said Orion update versions 2019.4 through 2020.2.1 (released between March 2020 and June 2020) also contain the malware.
If your organization uses any of the affected Orion affected platforms/products, we recommend you immediately investigate what versions you are running and take the below steps.
What to Do
Affected organizations should immediately power down or disconnect from their network SolarWinds Orion products, versions 2019.4 through 2020.2.1 HF1.
SolarWinds recommends the following immediate actions.
If you cannot upgrade immediately, SolarWinds recommends installing your Orion Platform behind firewalls, disabling internet access for the Orion Platform, and limiting the ports and connections to only what is necessary. For more information, read SolarWinds Orion Platform best practices configurations and the entire SolarWinds security advisory.
We provide leading comprehensive insurance coverage combined with essential cybersecurity prevention and detection tools.
One Minster Court
Mincing Lane
London
EC3R 7AA
Interested in Cyber Insurance?
Recent Comments