The healthcare sector experienced a surge in web application attacks in December when the distribution of the first COVID-19 vaccines began, according to new data from Imperva.
Attacks increased 51% last month from November, an industry increasingly targeted by cyber-criminals over the past year due to the global pandemic.
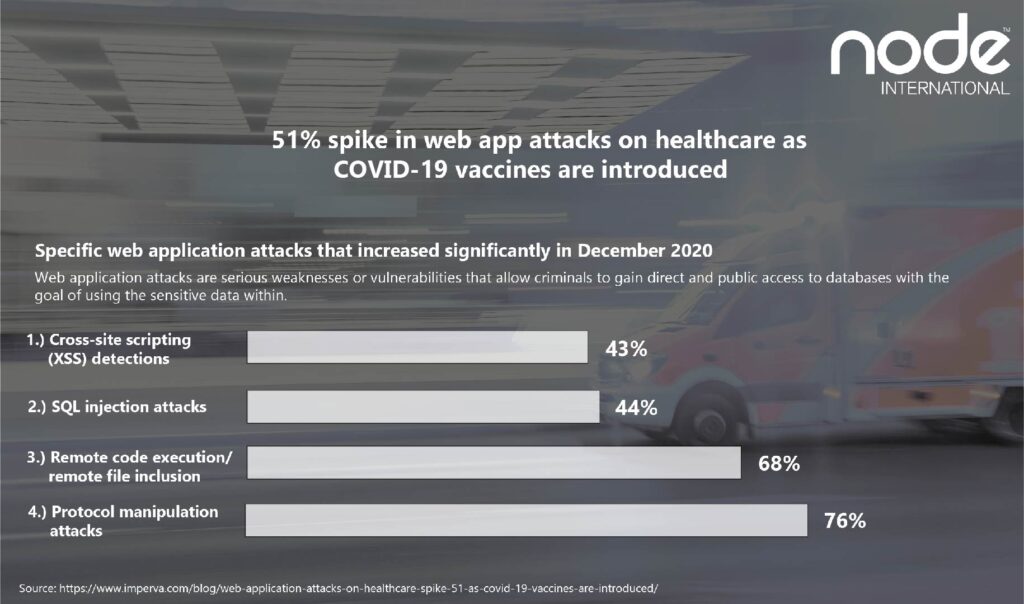
Web application attacks are serious weaknesses or vulnerabilities that allow criminals to gain direct and public access to databases with the goal of using the sensitive data within. Many of these databases contain valuable information such as personal data and financial details, meaning they are frequently targeted.
Four specific web application attacks saw the largest increases in December:
1.) Cross-site scripting (XSS) detections
2.) SQL injection attacks
3.) Remote code execution/remote file inclusion
4.) Protocol manipulation attack
How can healthcare organisations reduce web application attacks?
1.) Web Application Firewalls (WAFs): A vital defence for critical applications and data. WAF controls access to web applications using rules designed to recognise and restrict suspicious activity, such as SQLi, XSS and exploitation of vulnerabilities. By continuously updating the rules they are prepared to catch the latest attack and exploitation techniques before they can harm important resources.
2. Vulnerability Scanning and Security Testing: The fact web applications connect external users to data and services easily makes them big targets for attackers. Scanning and testing databases, networks and applications can help find where the vulnerabilities are and how to mitigate them.
3. Secure Development Training: Provide your developers, testers, project managers and architects with the latest information regarding secure software development. Ensure there is a baseline of security awareness so staff can confidently design, build and deploy secure software and applications.
Terry Ray, Imperva, said that 2020 has been an “unprecedented year” of cyber activity, with global healthcare organizations (HCOs) experiencing 187 million attacks per month on average. That’s almost 500 attacks per HCO each month, a 10% increase year-on-year.
The US, Brazil, UK and Canada were the top countries targeted last year.
Ray believes that Healthcare’s reliance on third-party applications to save time and money may have exposed them.
“While there are sometimes business advantages to third-party applications, the risks include: patching only on the vendor’s timeline, known exploits that are widely publicized and constant zero-day research on widely used third-party tools and APIs.”
Ray also highlighted how exploiting web application vulnerabilities is the most common cyber attacks directed at healthcare organisations.
“Reliance on JavaScript APIs and third-party applications creates a threat landscape of more complex, automated, and opportunistic cybersecurity risks that are increasingly challenging for all organizations to detect and stop. And while ransomware attacks commonly land healthcare organizations in the news, it’s only the vulnerable application front-end to all healthcare data that experiences the variety and volume of daily attacks noted above.”
In just the first three days of 2021, Imperva saw a 43% increase in data leakage.
